Trying to remotely invoke Computer Management on newly installed Server Core instance invokes warning by default:
To enable Computer Management from remote Server Manager instance in Windows Server Core:
open regedit - type regedit, hit enter
navigate:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\COM3
switch Com+Enabled DWORD from 0 to 1
or, change the regsitry from the command line:
reg add HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\COM3 /v Com+Enabled /t REG_DWORD /d /1 /f
(if need to change back, change /d 1 flag to /d 0)
lastly, run these two firewall opening commands:
netsh advfirewall firewall set rule group="Windows Management Instrumentation (WMI)" new enable=yes
netsh advfirewall firewall set rule group="Remote Event Log Management" new enable=yes
If still not connecting with Computer Management, try this:
Set-NetFirewallRule -Name "WMI-RPCSS-In-TCP" -Profile Domain -Enabled True
Now you should have access to remote Computer Management option in Server Manager
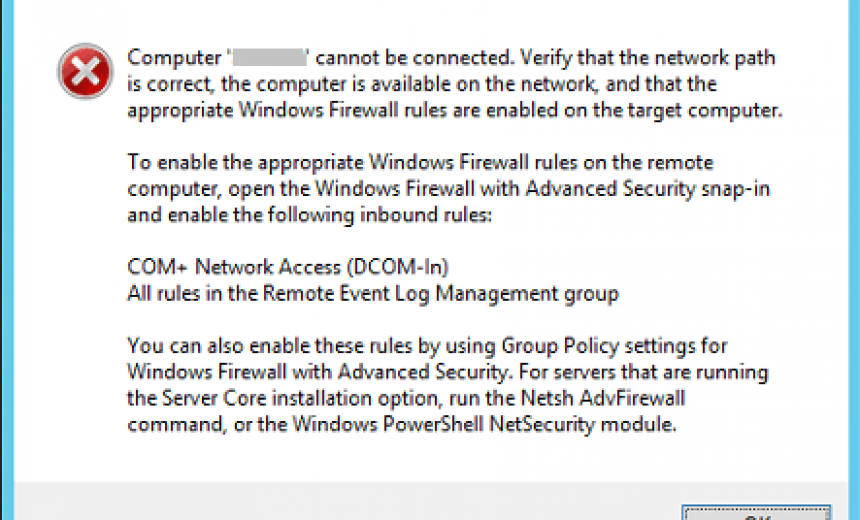
I have tested all of the above methods and even the methods related to Group Policy, but I still get the above error.